Teach children about cyber security by playing Capture the Flag
Since the beginning of my studies (yes, we are going way back), I have given guest lectures at primary and secondary schools. It mainly started to make girls more enthusiastic about technical / IT studies by providing lessons about web & app design (within VHTO’s DigiVITA project), I liked it so much that I still love and enjoy these guest lessons. Now they are no longer about HTML and CSS, but about cyber security and safety on the internet.
As part of these guest lessons, I also organize the Summer School every year, where more than 50 children between the ages of 8 and 15 can choose between two different areas: the social engineering game and a technical Capture the Flag. The social engineering game was aimed at children from 8 to 11 years old, older children from 12 years old could get started with the Capture the Flag. A Capture the Flag is an online competition where teams have to look for ‘flags’. These flags are hidden in, for example, a web application; you will only see them when you have successfully solved a challenge. Security experts or ethical hackers use this to practice hacking, but it also works well in school classes because of the game element. You will soon realize how easy it is to get in and choose a stronger password or enable two-step verification.
I wrote the platform for the Capture the Flag in Laravel. Since different ages had to work with varying skill levels, I wanted to make the platform as simple as possible (and I couldn’t find that in existing platforms). Besides, I don’t mind coding from time to time :). To test the platform and the challenges in all ways, we played a practice round with many security specialists. If you still find something, please let me know!
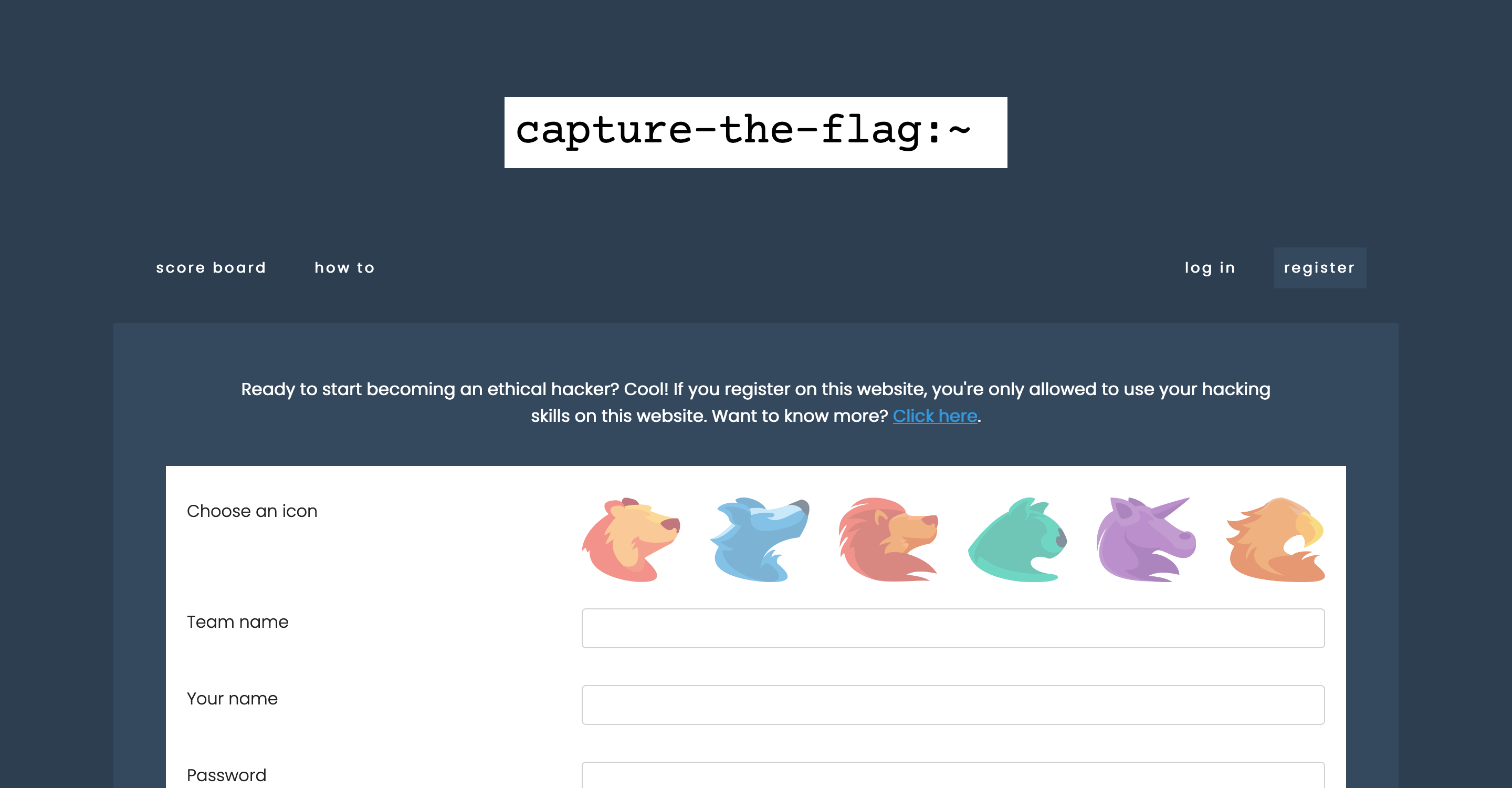
You can register as a new team on the landing screen. Do not forget to choose an icon that suits your personality well (hehe). A CTF code was set as a requirement to place students in the right classroom. Only students in your classroom will be placed on the scoreboard.
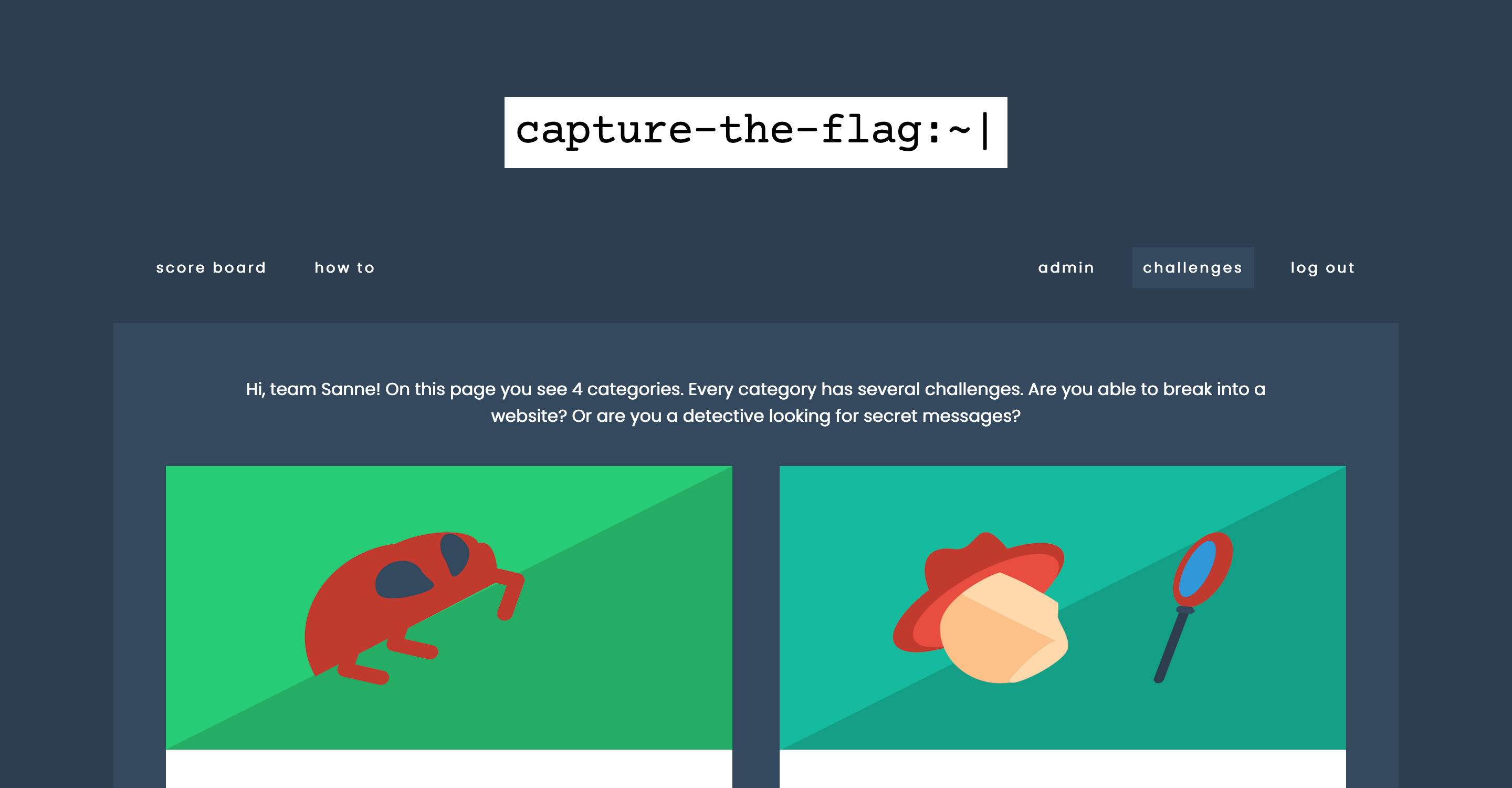
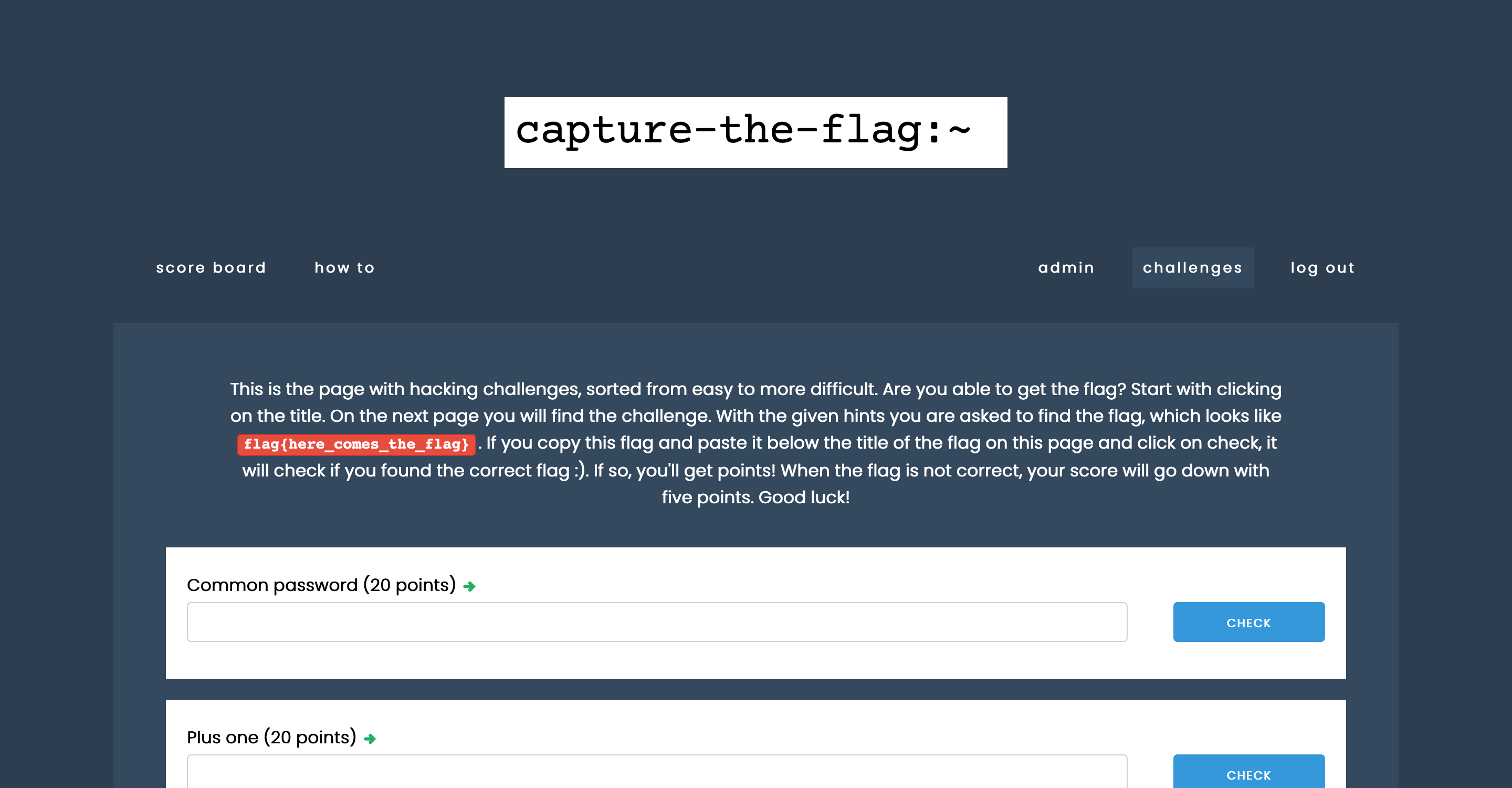
On the left screenshot, an overview screen with several categories is shown. At the moment, these are hacking, forensics, crypto, and coding. Per category, a record is kept of how much you have already solved. On the right screenshot, you can see how the challenges are displayed per category. The challenges are sorted by the difficulty in a list, where the title is the link to the challenge. There is an input field for each challenge: the flag found must be entered here.
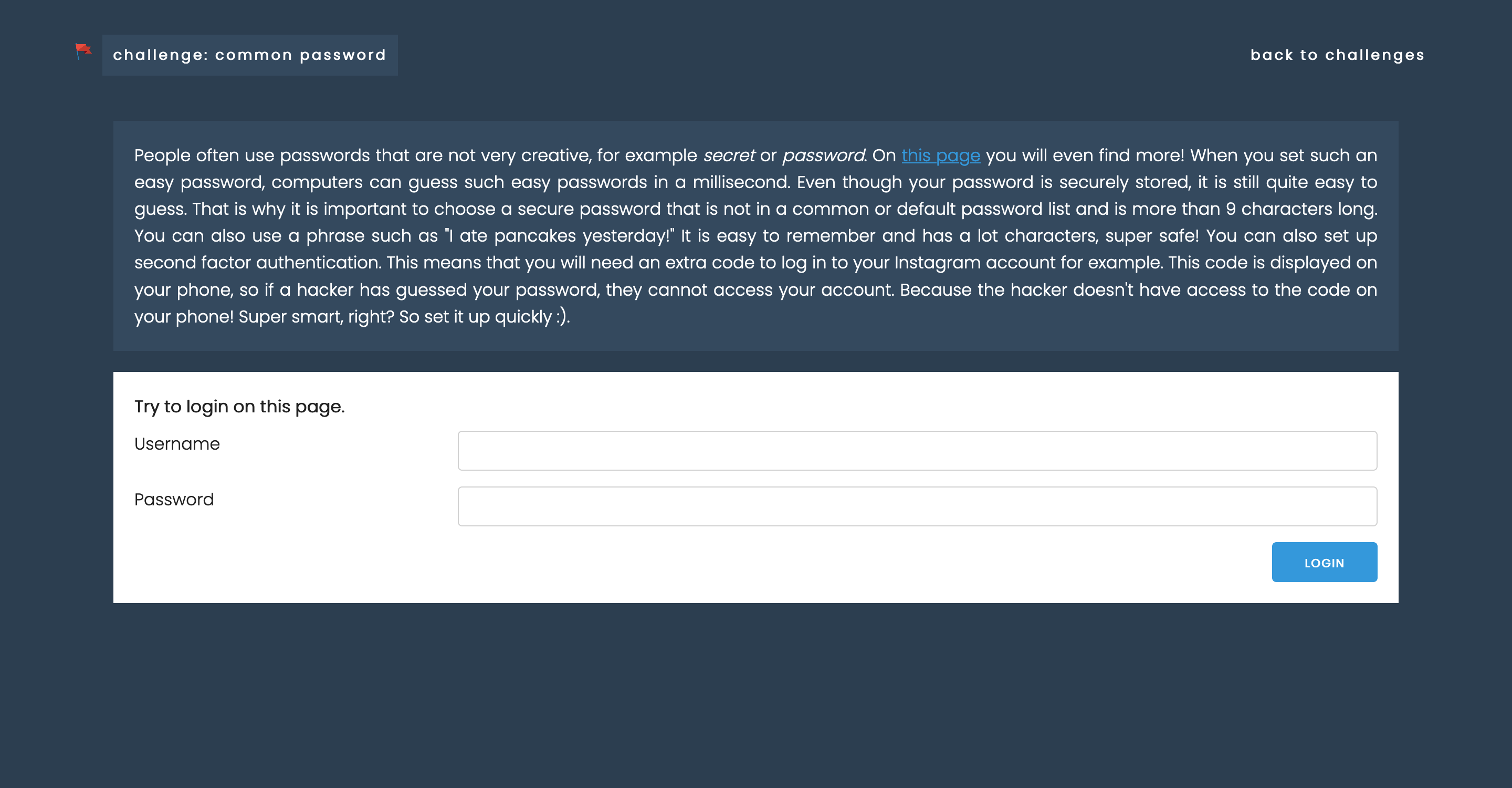
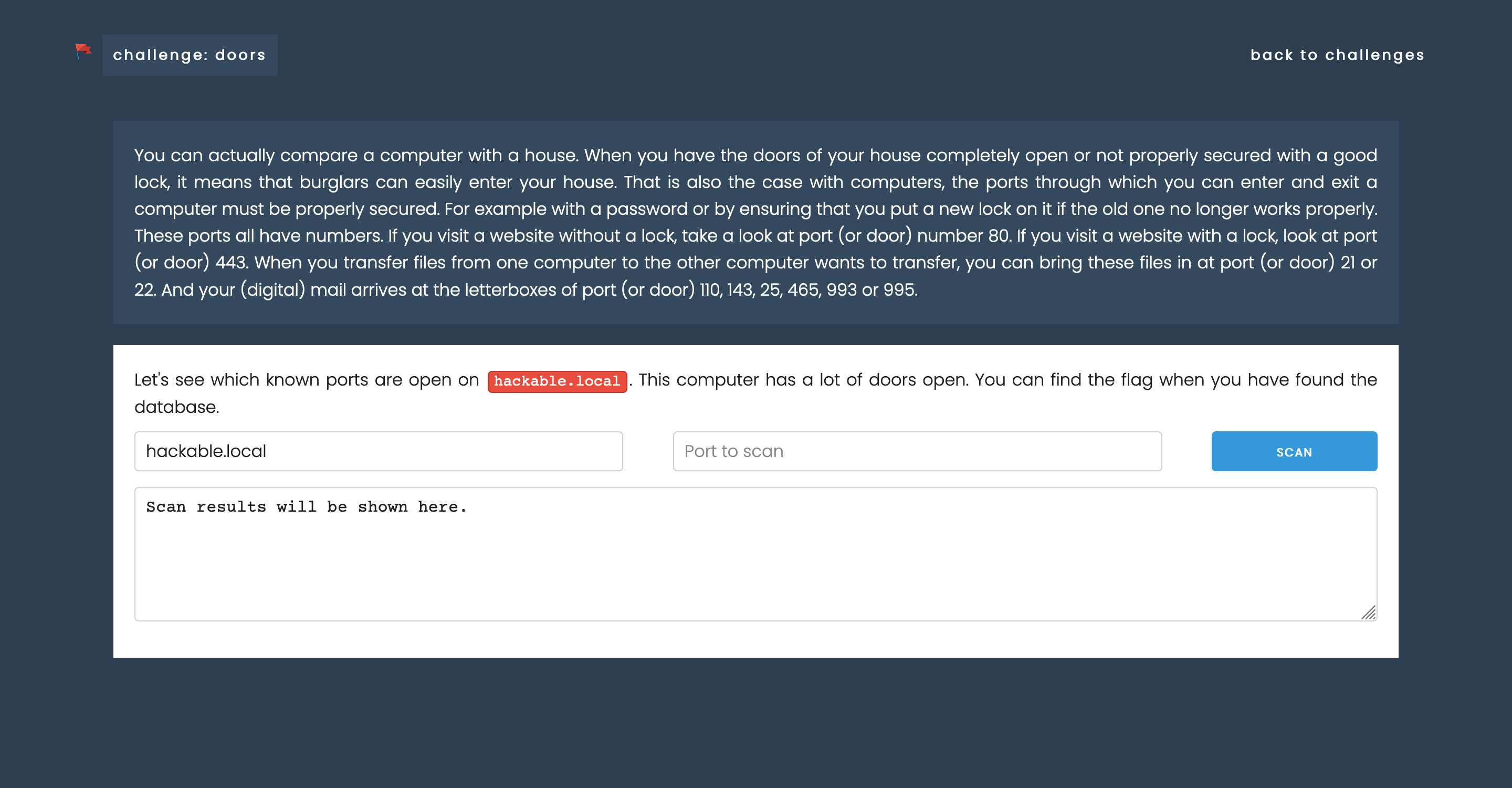
The above screenshots show two challenges: ‘Common password’, where you have to try to log in with frequently used usernames and passwords and ‘Doors’, a challenge where you have to see which ports are open on a server to gain entry. Let’s see how to solve the first challenge. By clicking on the link, you will find a Wikipedia page about the most commonly used passwords. You should try this manually (or automatically if you’re a 1337 hacker). However, you don’t know the username, but you will easily find out if you read the error message correctly. Do you have the username and password correct? Then you get a flag.
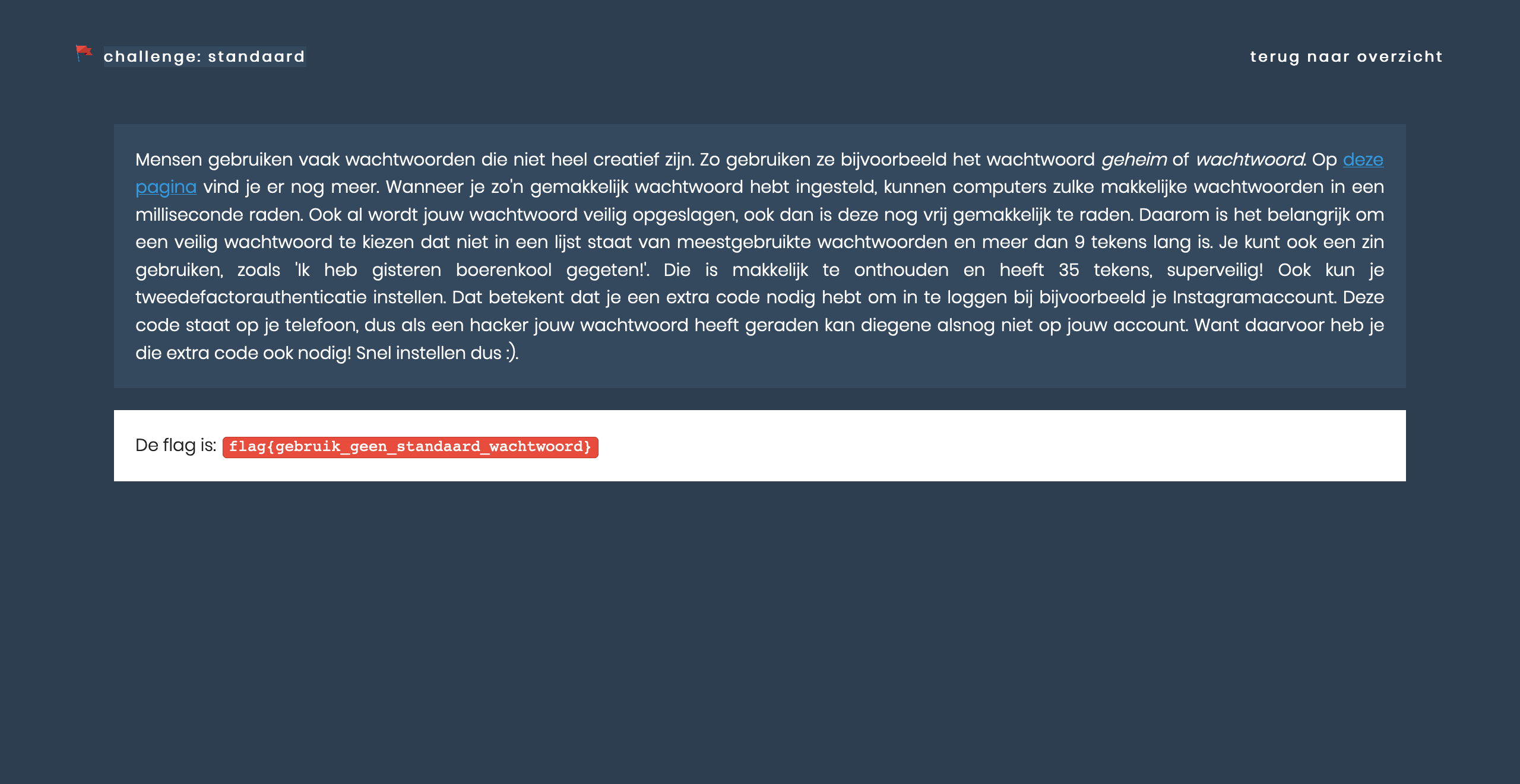
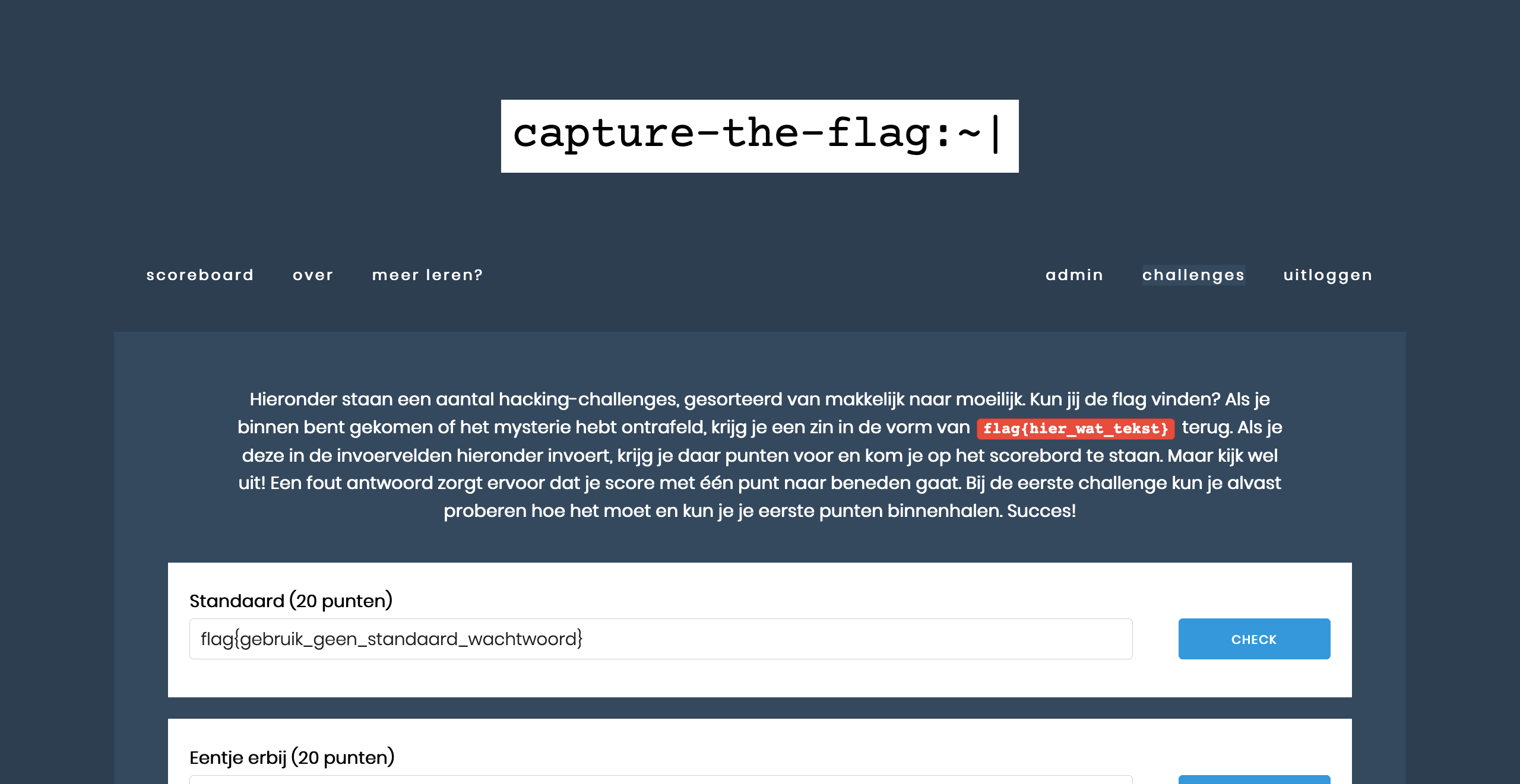
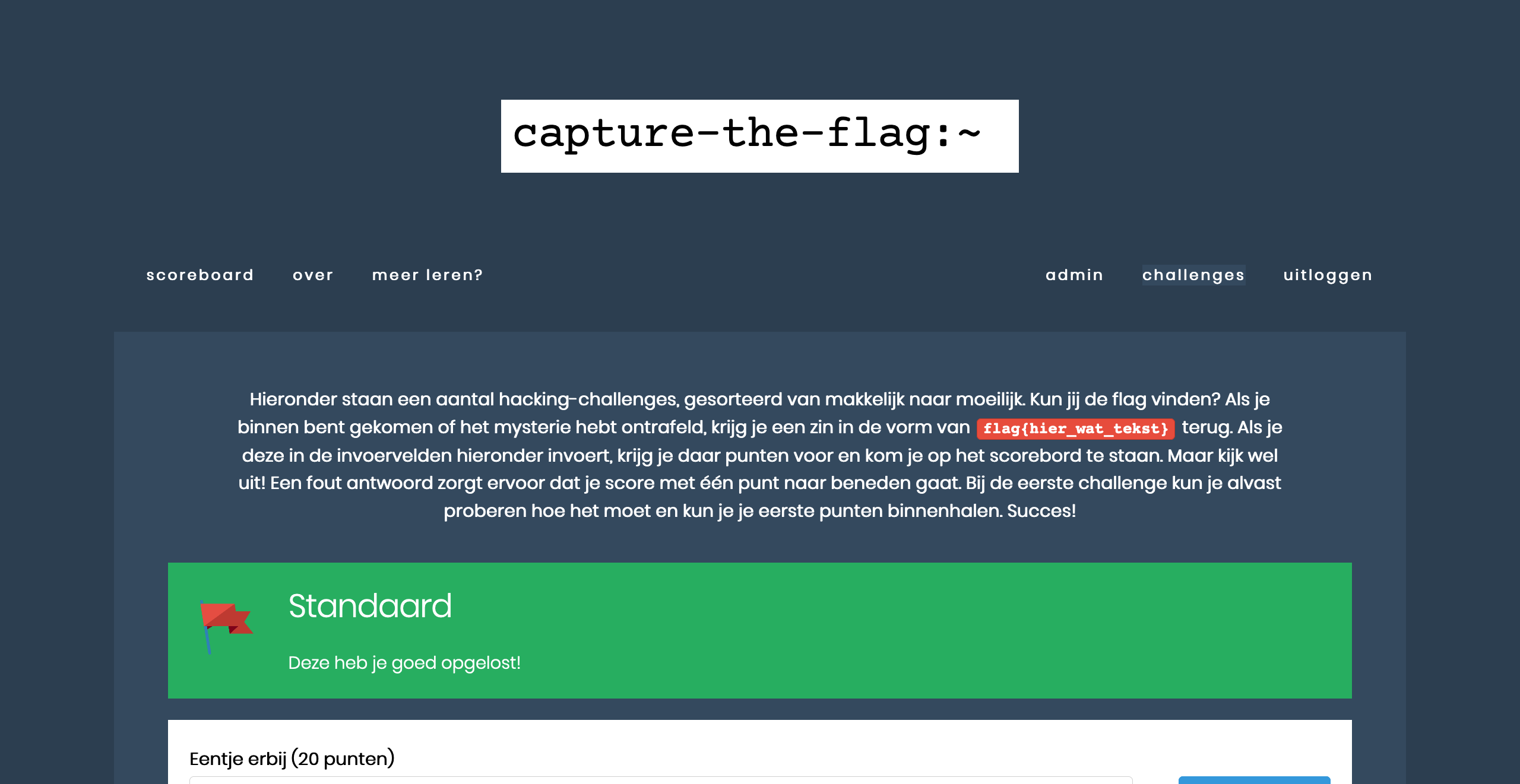
On the left, you see the flag. If you enter this in the input field below the correct challenge name (second screenshot), you will receive points (third screenshot), and the challenge will be indicated as ‘solved’.
Do you also want to use this in your class or with your kids? At https://ctf.hackchallengesforkids.com you can visit the CTF environment, including about 30 challenges (and more to come!). You will need a CTF scode to play it with your students. You can request this by sending a Twitter DM, a LinkedIn message or by sending an email to ctf [at] hackchallenges [dot] nl.