Phish like an APT: phenomenal pretexting for persuasive phishing
tldr; This blog post is nothing more than an essay on why we should think about what kind of phishing email we send out during adversary emulation assignments. Of course, initial foothold is often gained (by adversaries) by using a weaponized spear-phishing email. But have you ever wondered what phishing strategy real-world adversaries use? And how these scenarios compare with the scenarios that you use during your adversary emulation? Find an overview of four of the most used adversaries and their characteristics on this page.
If you did, you probably found out that there’s a lot of research about adversary techniques, tactics, and procedures, like the use of specific malware or attack vectors. Still, there are few public resources on which techniques those attackers use to convince a non-suspecting person to aid them in their operation. In this blog post, an analysis is presented of hundreds of phishing emails that were used in actual campaigns. All characteristics of an email, like the method of influence, tone of speech, and used technologies, are classified and measures how well a phishing campaign is designed, scoring from “obvious spam” to “near-realistic original mail.” By comparing and measuring the state of these phishing emails, we can learn more about how certain groups operate and how much “effort” they put into their scenarios. Essential knowledge for both attackers and defenders.
So let’s start with the spear-phishing technique. In the last couple of years, more than 90% of all cyber attacks begin with a spear-phishing email1. Why? Because “it just works.” As mentioned earlier in this blog post, people interact with phishing emails because of a lack of sufficient security awareness training or because they’re distracted at that time - like being undercaffeinated or stressed after a day full of Teams meetings. We have to make decisions all day, every day. Having sufficient security awareness means the information in the newly delivered phishing email is associated with existing patterns, just like mental shortcuts. So what do phishers do? Use an influence technique to make that decision-making a little bit easier for you (thanks!).
Principles of influence used by adversaries
These techniques (also covered in the earlier mentioned blog post) are reciprocation, scarcity, authority, liking, and social proof2. But how do adversaries use these principles of influence to persuade the recipient to interact with the email?
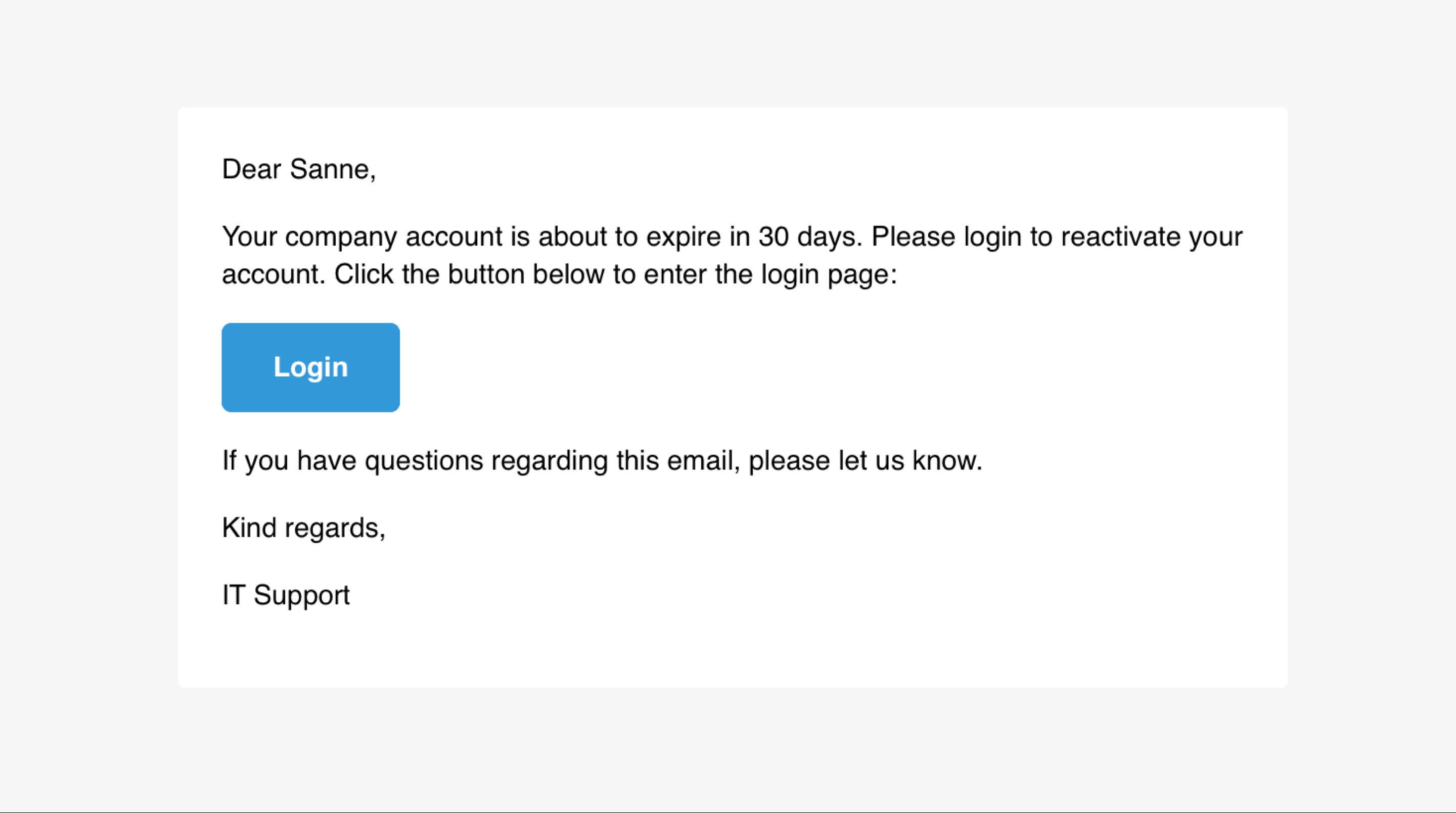
Principle of reciprocation. I do this for you and you do this for me, so I give something back. The recipient of the email might feel indebted and returns the ‘favor.’ In this case (see example) the recipient got notified by the IT service desk that the account was about to expire. You’re happy that someone notifies you before your account expires, so you fill in the credentials.
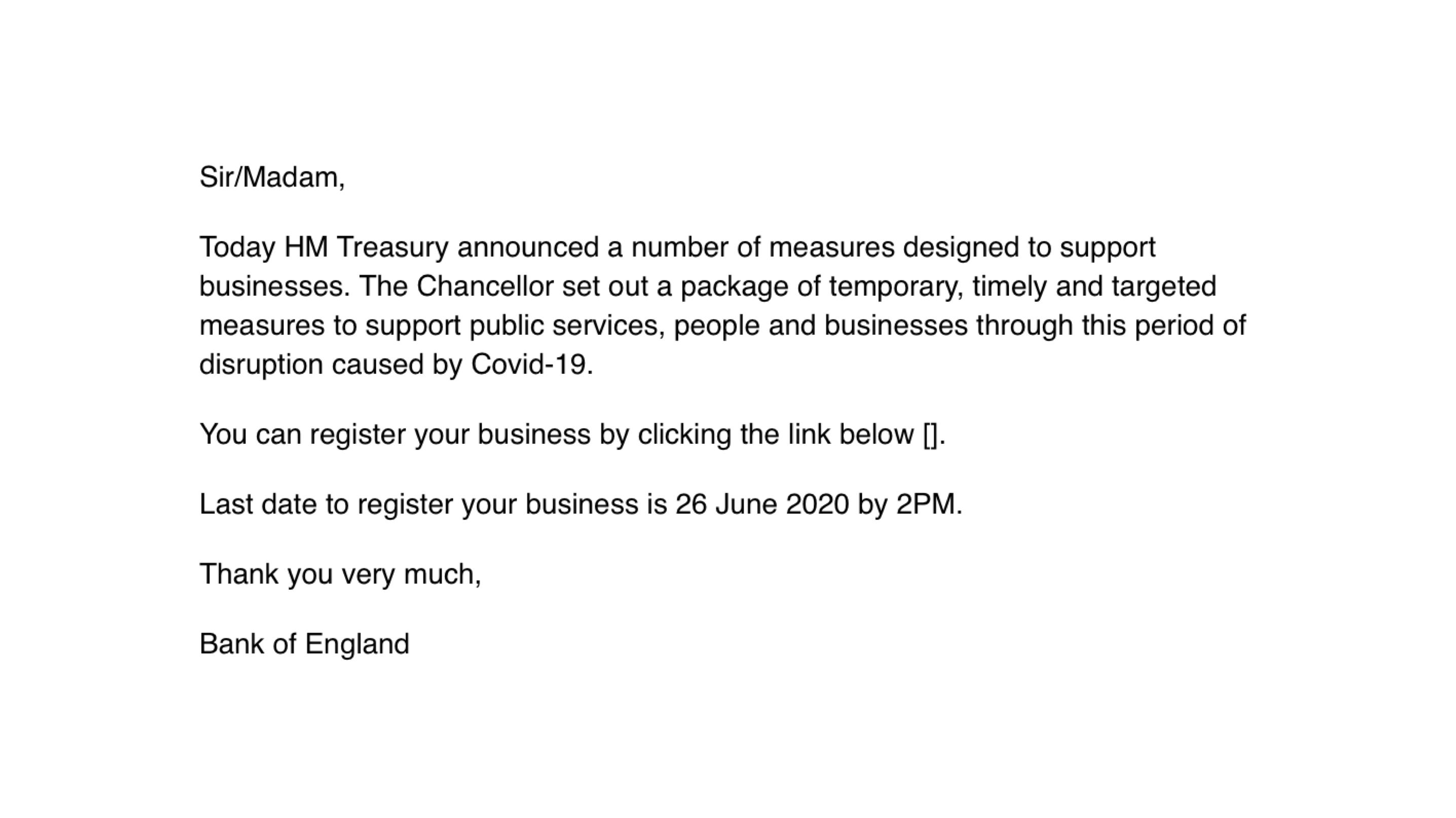
Principle of scarcity. When someone has access for only a short period. In this example - a confirmed phishing mail sent by APT38 (Lazarus Group)3 - the recipient gets an offer that’s valid for only a couple of days. You feel you need to act immediately before that offer is invalid. This is why marketing people would be great phishers: when you didn’t finish your order at a website and get a discount email for a limited time, the influence of scarcity is applied. Smart marketeers.
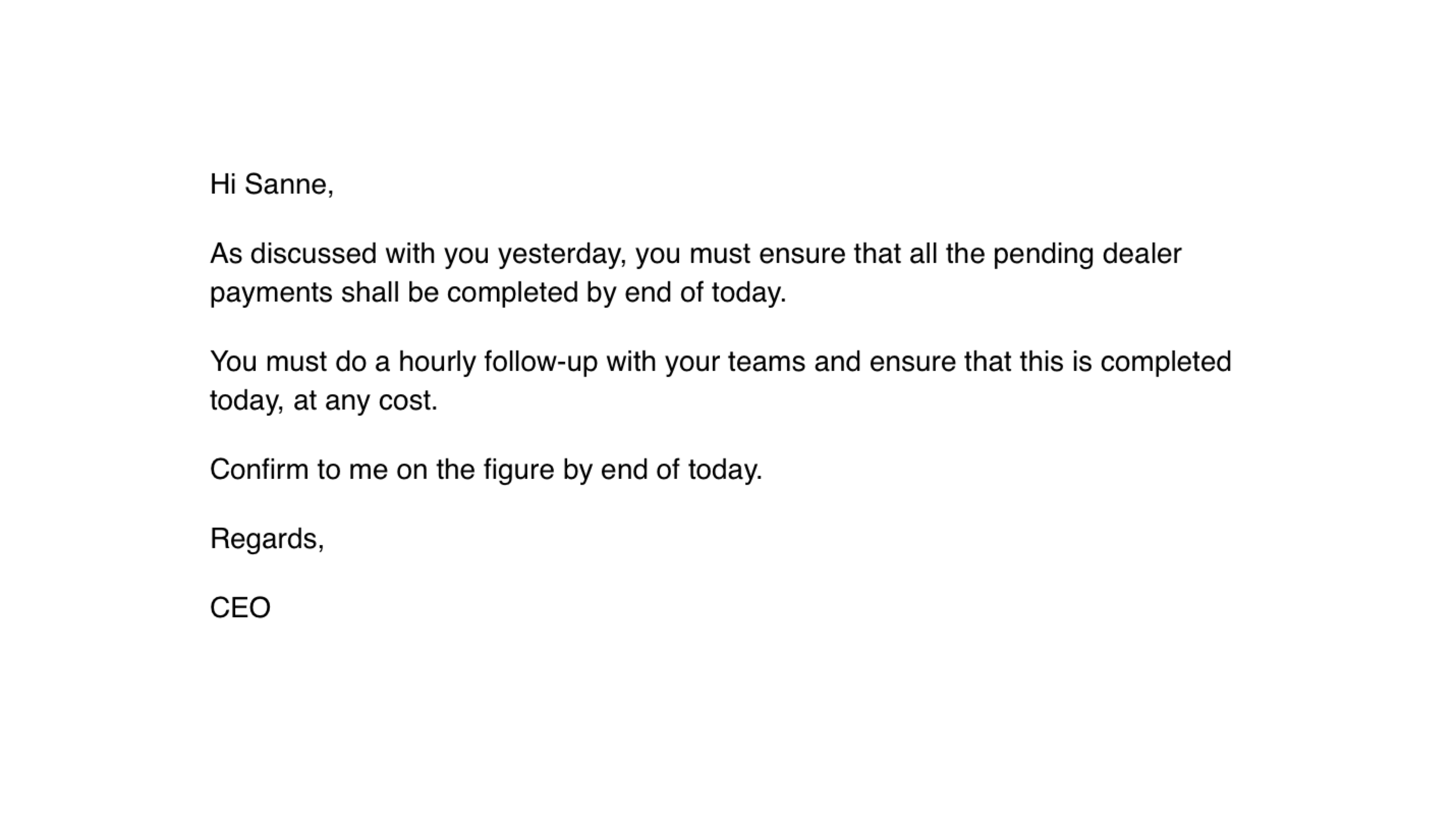
Principle of authority. You feel you need to obey, whether it’s the CEO of the company or a known authority like the Police. This principle is used in CEO fraud: an email is sent by the CEO to the finance department to get payment done. TA505, a Russian criminal group, sent the displayed email. A weaponized Excel file with pending charges was attached to this email.
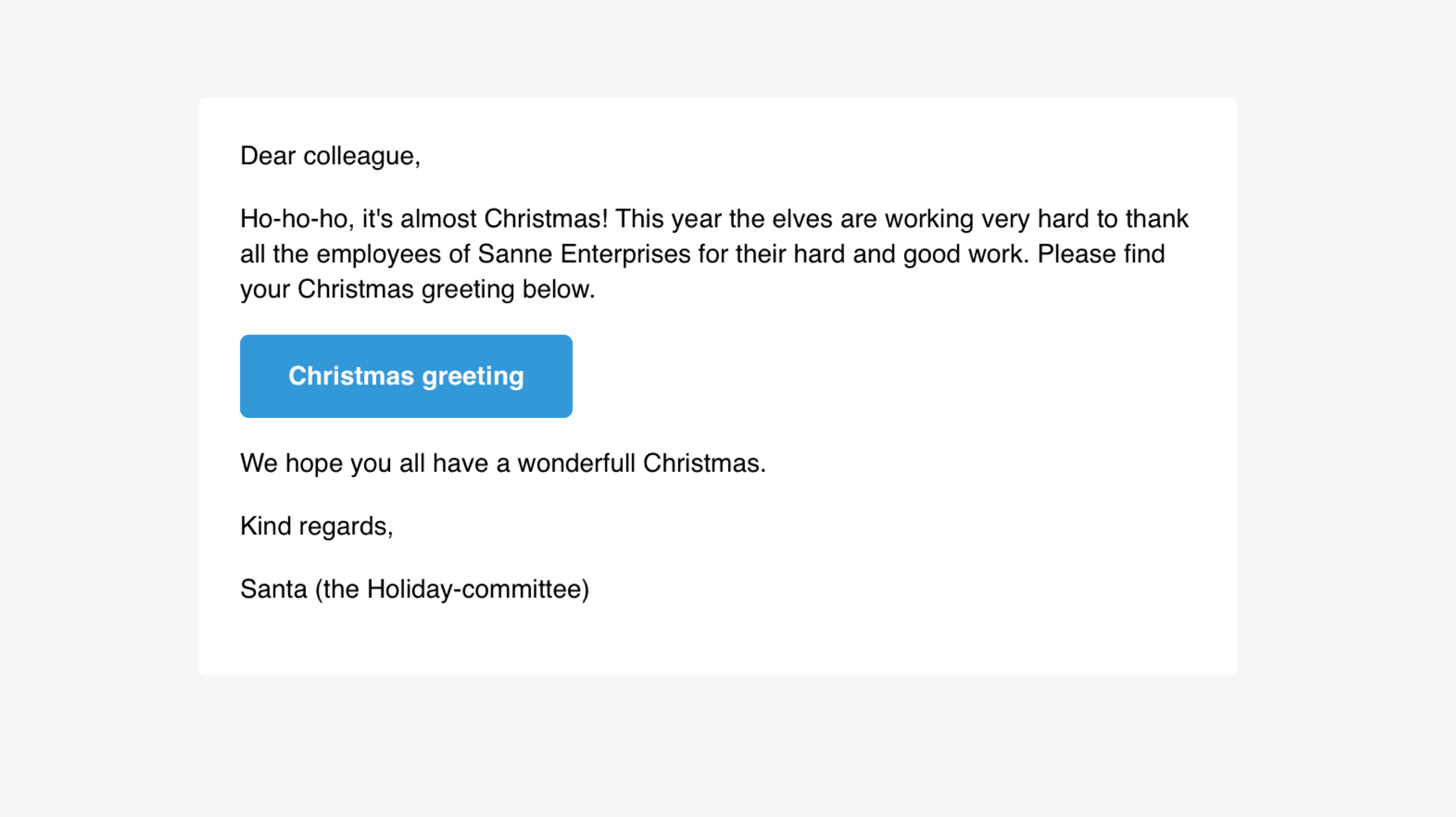
Principle of liking. Do we have shared interests? Do people already know me and like me? If yes, the principle of liking could be used to persuade the recipient. This email is slightly inspired by APT28, who used a Christmas theme4 - with Santa as the sender of the email - with a weaponized Christmas greeting in the attachment.

All elements of an email or message contribute to the influence of the email: it’s the full package of the sender, the email body, the theme and the goal of the email.
The phishing classifying model
In this previous blog post, a classifying model was created to measure the scenario of an email. This model is reused to classify adversary emails and compare the characteristics over multiple groups. In addition, the medium the message is sent on, like email or social media accounts, is added to this model as spear-phishing of adversaries didn’t only happen via email. The classifying model is displayed below.
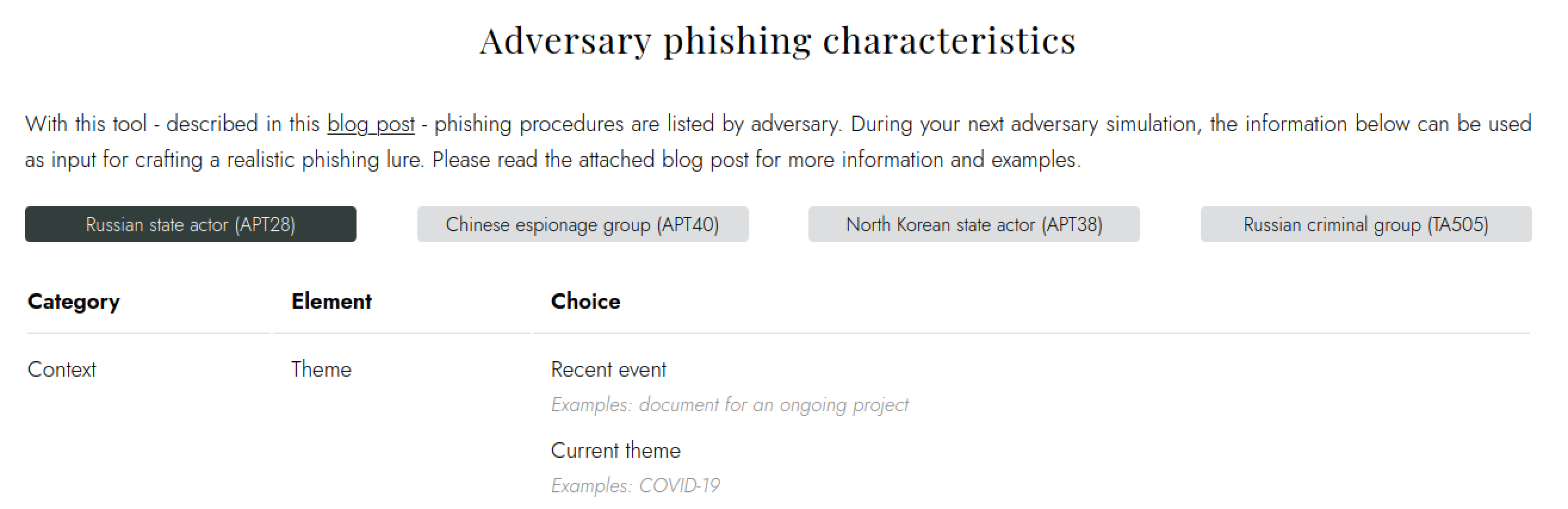
| Category | Element | Choice |
|---|---|---|
| Context | Theme | Important value, recent event, current theme, timeless activity |
| Sender | Own organization, known/unknown organization, private person | |
| Goal | Obtain credentials or access, initiate offline action | |
| Principle of influence | Reciprocation, scarcity, authority, liking, social proof | |
| Medium | Email, LinkedIn, Twitter, WhatsApp, Telegram | |
| Content | Language and text | Correctness, clarity, engagement, delivery, style guide |
| Design | Copied corporate identity, neutral identity, plain text | |
| Personal information | Correct salutation, real names and personal information | |
| Domain name | Sender | Compromised mailbox, spoofed email address, expired domain name, typosquat domain name, irrelevant domain |
| URL to phishing website | Expired domain name, compromised website URL, typosquat domain, irrelevant domain, external platform or service | |
| Attachment or download | Document | Office documents, HTML page, archive file |
Each adversary is plotted on this model to show the difference between several adversaries.
Selecting the adversaries and creating the data set
The hardest part of researching adversary emails is - right - obtaining the adversary emails. It depends on the adversary and their motive: the minor progressive groups trying to let the victim download a dropper to install ransomware on your network will be more likely to send out more near-spam campaigns than espionage groups trying not to get detected. The first step is to select the adversaries for this research: which adversaries use (spear)phishing as a technique? For example, MITRE defined spear-phishing as technique T15665 with three sub techniques:
- Spear-phishing attachment - adversaries send emails to the victims with a malicious attachment added to the email, like a weaponized document or archive. The sender usually tries to convince the recipient to open the document and bypass protections (like the ‘Enable macros’ in Office documents).
- Spear-phishing link - the emails contain a link to an external website, like a (cloned) credential harvesting page or file download page (for example Dropbox or Google Drive) where a malicious document can be downloaded. In a few cases, a browser exploit is used to obtain access or data.
- Spear-phishing via service - the adversary makes use of an existing service or platform, like LinkedIn or WhatsApp, to deliver a document or just to gain trust from the recipient and then switch to a different platform, like a personal email account (which might have an easier to evade spam filter).
Groups using these phishing (sub)techniques are listed on the group pages of the ATT&CK framework or the page of each sub technique. During adversary emulations, threat analysis is performed to select a relevant threat group that poses the most significant risk for the organization. Generally, those threats are an insider threat, a big crime group, or a nation-state or proxy. The insider threat won’t be selected during this research as this attack won’t start with a spear-phishing email. Well, at least it’s unlikely.
Selecting the adversaries is dependent on the size of the data set available for the group. First, a list of groups matching the crime group or nation-state criteria + if they have the phishing technique listed as a used method is made. Based on this list, phishing emails will be gathered. Emails in .eml or .msg format are retrieved in these ways:
- From the brilliant guys from the Threat Intelligence department
- By scraping Twitter with a query consisting of the group name and keywords like “maldoc,” “phishing,” “IOC,” “github,” “virustotal,” “pastebin” Sometimes this will give you a direct link to the VirusTotal page of an email or the attachment, sometimes to a list of email IoCs6
- Browse through platforms like AlienVault Open Threat Exchange or Malpedia
- Check VirusTotal for each maldoc hash and check if this malicious document has an email parent
- Do an advanced search by checking out the results of the Thor APT scanner7 by Florian Roth
- Do an advanced search where the group name + the tag “attachment” form the search query to find only attachments of emails
- Search for specific malware families only used by particular groups and check if these are sent as an attachment
Next to creating a data set based on these search results, the data set is enriched with other types of data, like associated IoCs (phishing domains, maldocs) and screenshots published in research from threat intelligence providers. A part of the data set will be analyzed automatically by parsing the EML files. The sender name and subject will be checked from the header, and the body will be examined by the SpaCy package and the Grammarly API.
Based on the availability of this data plus the mentioned selection criteria, the following four adversaries are selected to plot on the created framework (hover for associated names): TA505, APT28, APT40, and APT38. By clicking on the screenshot below, you will find a complete overview of all characteristics mentioned in this post:
TA505 (click for full overview)
A better word for TA505 might be ‘lazy mode.’ A lot of emails were available for this threat actor. Not surprising as this threat actor has a financial motive and is more leaned towards a spam campaign than spear-phishing. As they have many people associated with this group, it’s a little bit harder to define a ‘typical’ email as the level of the email (writing, theme, etc) differs. However, different similarities were found, like how they compose their emails: they are not personal and could be sent to everyone, for example. It’s hard to find a principle of influence in the text of the emails - as they are mostly quite plain with email bodies like “This email is sent automatically” or “Please see attachment” - but the principle of liking pr scarcity is the most likely principle they use in their emails. As this threat actor pretends to be a victim’s colleague, they use the advantage of the relationship between the sender and the recipient by applying some time pressure from time to time.
When zooming in on the layout and text of the email, no layout or corporate branding is present in almost all the cases, just plain text. URLs to malicious downloads are included in the email and look legit as words as ‘onedrive’ and ‘dropbox’ are used. In other cases, just a malicious document like an Excel document or HTML page are attached to the email.
The most noteworthy attribute of the email is the sender. In order to prevent having the email flagged as ‘spam’, this threat actor uses already compromised email accounts to send emails to their victims as they have the correct DKIM and DMARC settings. Multiple exact copies of one email, sent to various employees of different organizations with the subject ‘pending payments to be cleared today, immediately’ are sent from the same sender name (R.V. KRISHNA PRASAD) but with different email addresses. The sender names don’t match the sender’s email addresses.
APT28 (click for full overview)
A more advanced group is definitely APT28, a Russian group associated with the GRU. Emails sent by this adversary show different principles of influence, like the influence of liking and authority. For example, the group pretends to be a colleague or manager by sending emails with copied internal corporate identity of the company and spoofed email addresses they are mimicking. By choosing authorities like Google, they gain trust from the victims and persuade them into interacting with the email. So, in short: they use an authority for external to internal and a colleague when the email is from internal to internal.
The email body uses plain text, sometimes with minor changes (like a different font color) or copied corporate identity. The sender’s email addresses are spoofed or use a typosquatting technique - replacing letters by similar letters - or have a predictable pattern: office365-onedrive.com is used as a link in an email instead of the legit URL onedrive.office365.com, and natio-int.com is used instead of the legit URL nato.int. Next to URLs in the document redirecting to a credential harvesting page or malware download page, weaponized attachments like Word documents, Word template files, and archive files are added as an attachment.
Emails of this adversary are hard to find, so make sure not to send too many emails to employees of the organization you are Red Teaming.
APT40 (click for full overview)
The Chinese attributed group APT40 is all in for relevant themes for the recipient. By using the influence of liking, they bring emails with local news, activities, and events as the central theme. Victims are selected and profiled by scraping their social media accounts and other open sources. The emails of this adversary vary in how hard they are in distinguishing them from realistic emails: sometimes terrible grammar is found in their emails, sometimes it’s pretty sophisticated. People who interacted with this adversary experience outstanding initial emails, but when this group replied to the recipient’s question (like ‘how do I enable macros?’), the email body showed several flaws. This might indicate that someone is asked to compose the initial email but is not engaged with further correspondence.
The group tries to reach their goal by adding malicious documents as an attachment or hosting them on Google Drive and supply a link in the email. In many cases, a payload redirects the victim to the legit document after being downloaded and executed.
APT38 (click for full overview)
The last one and definitely a favorite is the North-Korean government-affiliated adversary APT38, also known as the Lazarus Group. They know how to influence (#influencer). Trust with the victim is built by creating full characters or impersonating people. This includes creating social media profiles for these characters, using LinkedIn, Twitter, Telegram, and email. As they carefully pick their victims, they also put effort into creating relevant profiles for the victim. The group, for example, adds your LinkedIn connections to their connections to gain trust. Because if your contacts trust the adversary, you will likely do the same.
Chaining different methods and services is typical for this attacker. For example, start the conversation on LinkedIn or Twitter, switch to Telegram or personal email to send information that can be used to compromise the victim. Email addresses are spoofed from real people, or a fictitious company is created, like a recruitment company. In the latter case, the name is not crucial as recruitment services with a random name still sound like a recruitment service. In addition, the language and form of speech used in their messages are adapted to the victim’s way of writing but are not always flawless. Dropbox and OneDrive are used platforms to host weaponized documents for the victim to download.
Your next adversary emulation
With this pitch, the phishing characteristics of four adversaries are outlined. During the next adversary emulation, I would encourage not to just grab a default scenario from the shelf that is proven to work but dive into the characteristics of an adversary phishing scenario. Be more creative and keep the principles of influence in mind when crafting the email itself. Of course, actual adversary operations could take months or years and adversary emulations will probably take weeks. They can also put more effort into their tooling and emails, but keep these characteristics as inspiration would definitely upgrade your adversary emulation.
This little research is entirely dependent on a good data set. If you have more adversary emails (EML or MSG or screenshots), this model can be finetuned and more reliable. Please hit me up if so!
This research was presented on DEF CON (Adversary Village):